How To Break Into Someone’s Phone In 2022?

Contents
Breaking into someone’s phone is very exciting but difficult too. If you’re eager and interested and want to know how to hack a phone, this article’s for you. It populates multiple methods and quick steps that you can follow to hack someone’s phone with just their number.
Is It Possible To Hack Someone’s Phone With Just Their Number?
First things first- is it really possible to gain access to someone’s phone with their number without their permission? Yes, it’s quite possible. MacAfee, one of the leading anti-virus maker suggest that SS7 signaling system connects all the cell phones worldwide.
To gain access to someone’s phone with just their number, you need to gain access to this signaling system. Once you intrude the system, you can read messages, forward and record calls and do pretty much anything with the target device.
Why mSpy- Quick Details
How to hack into someone’s phone? Go for mSpy. This tool facilitates intrusion while keeping the phone owner unaware of spying attempts. It allows tracking their activities on their cell phone such as calls, SMS, activities performed over the internet, etc.
The reason for choosing mSpy is you can get started easily, and the process is fairly simple. While you can get started immediately, there’s no way you’ll be caught tracking the targeted cell phone. The makers have over a decade of experience in the development field and have served millions of happy customers worldwide. This app supports over 180 countries while housing 36+ features in a single mobile app package.
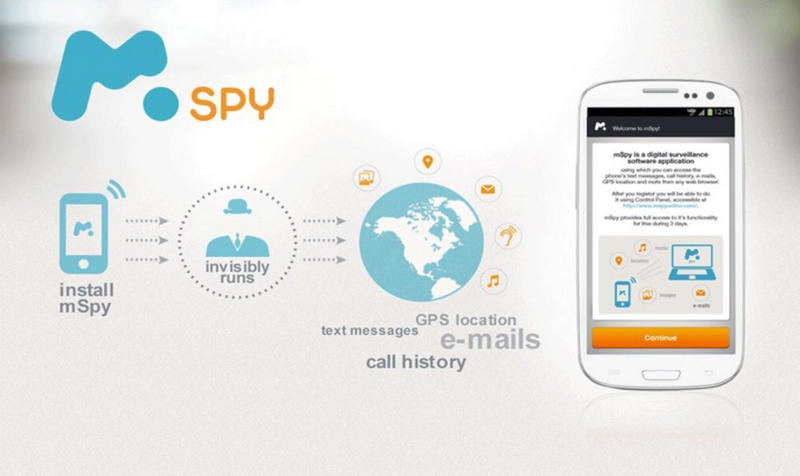
Advantages Of mSpy
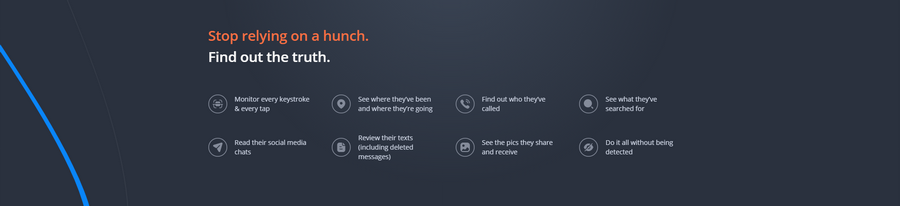
Let’s focus on a few outstanding benefits of using mSpy:
- It gives the capability to view every tap that the user makes on their phone.
- You can view their travel history. mSpy allows tracking their current geographical location.
- mSpy can reveal the call details and show the device’s internet browsing history.
- You can read the user’s social media chats and SMS messages.
- mSpy is a great tool to monitor the data that the phone owner shared with other people.
The best part of going for mSpy is that you can get started in three simple steps.
Using Keylogger To Break Into Social Media Accounts and Email
Want to know how to hack a phone? Let’s get started with the Keylogger feature by mSpy.
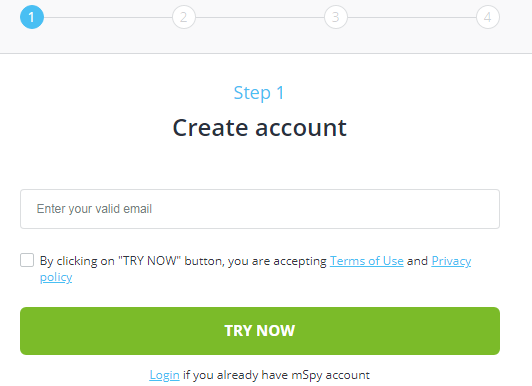
- Create a free account on the official website.
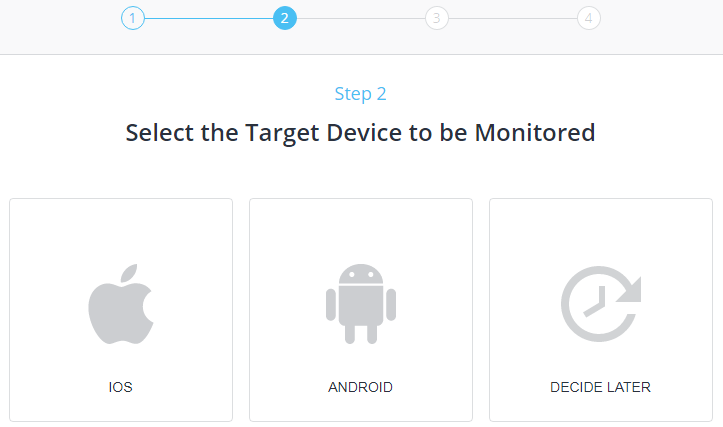
2. Select the target mobile phone’s Operating System. You’ll see an option “decide later.” Choose it to skip this step for now.
3. Choose a plan from the list based on your requirements. You should see multiple plans, their pricing, and the features that each plan supports.
4. Proceed and follow the on-screen guide. Finishing everything will hardly consume more than 2 minutes.
5. Visit your dashboard and navigate to “keylogger” from the menu.
6. The purpose of a keylogger is to read the social media messages that the phone owner shared. Keylogger feature will reveal all the messages that the user shared along with the timestamp of each message and app name.
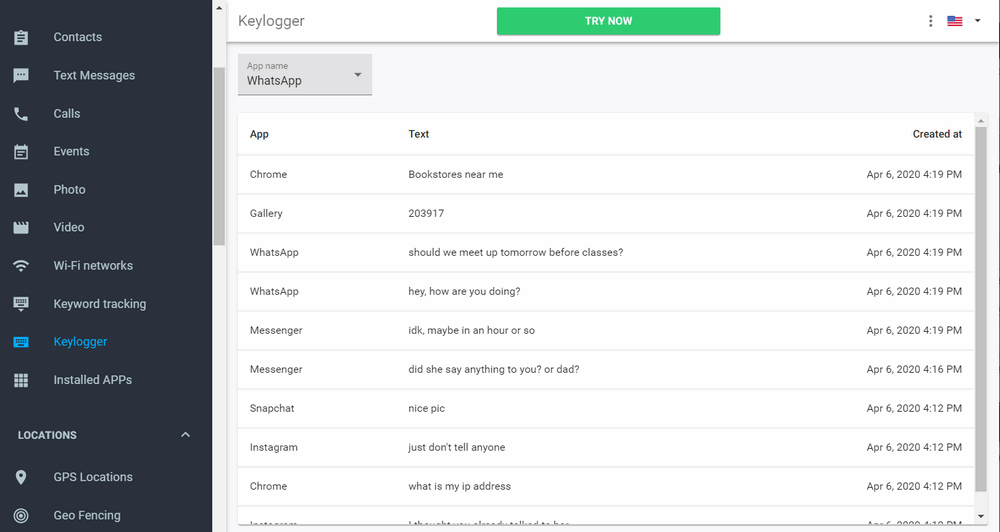
How To Hack Someone’s Phone Using mSpy?
Let’s see how to hack a phone number using mSpy. Follow these steps, and you’ll be good to begin shortly:
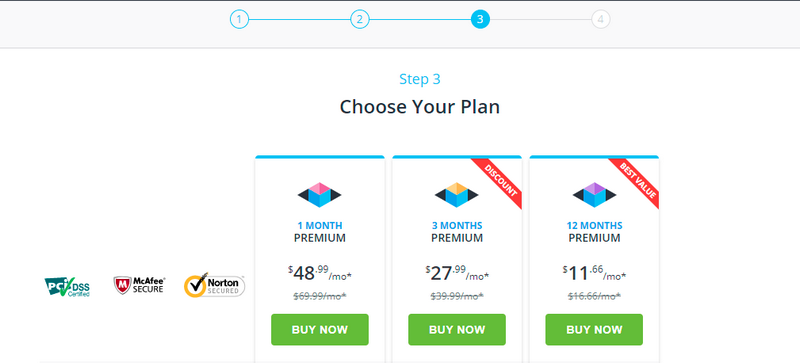
- Choose the desired subscription plan.
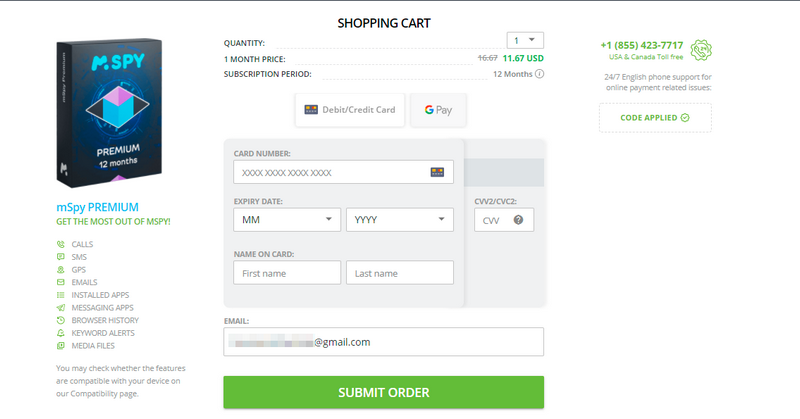
2. Proceed to the checkout. Enter your email address wherever asked to proceed. Click “submit order” and view your dashboard after making the payment.
3. On the navigation menu on the left, click the “add new device” button and follow the on-screen guide.
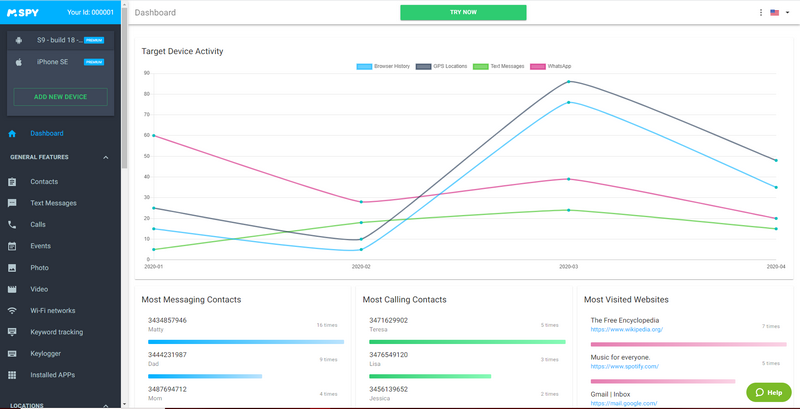
4. Return to the dashboard after adding the device and try the features listed in the menu.
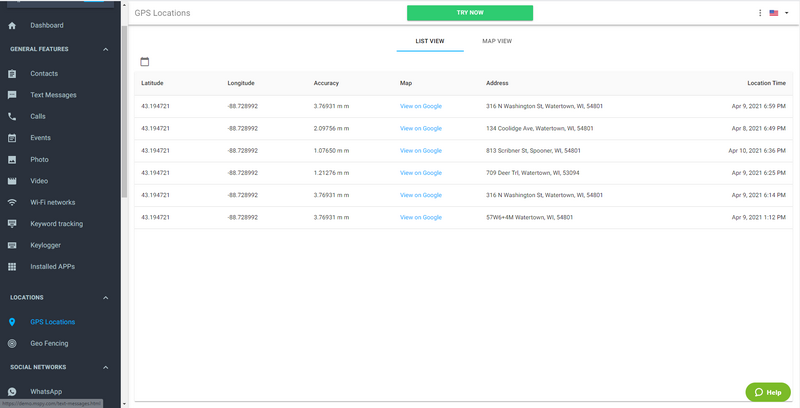
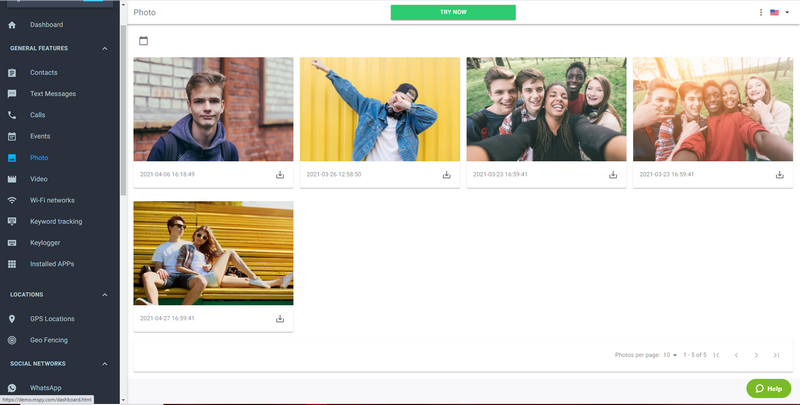
5. To view call history, click the “calls” option, click the “photo” or “video” option to peek into their gallery.
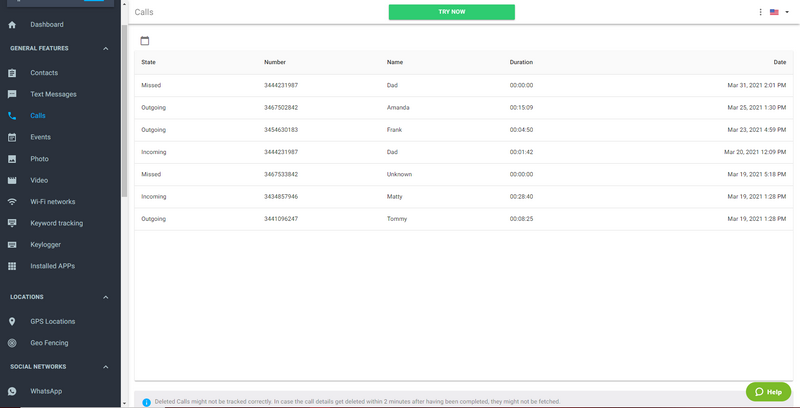
6. Browse through all the features listed in the left navigation menu. It’ll let you break into the phone using mSpy.
Additional Methods To Hack Mobile Phone Remotely
Surprisingly, there are alternate methods for breaking into someone’s device remotely. The process is pretty similar to mSpy, but the touch and feel will be completely different. Let’s cover those methods.
Minspy
Minspy is a spying app that lets you view the device’s GPS location, SMS and social media messages, data sharing details, etc. It houses a user-friendly interface that allows non-technical people to gain access to the targeted phone with little luck.
It’s a web-based tool, so you don’t need to download anything on your laptop or mobile phone. Visit the website to begin spying. The target device doesn’t necessarily have to be rooted (in the case of Android devices) or jailbreaked (in the case of iPhone).
Minspy supports targeting Android and iOS devices. However, in case you’re hacking an iPhone, access to the target device’s iCloud credentials is compulsory. This might sound like a major drawback since iCloud credentials are tricky to gather, leaving no room to hack into the target phone.

Spyier
This is yet another web-based application, just like mSpy, that aims to fulfill the need to hack into someone’s phone. It’s more like a spying tool but also gives some interesting tools to hack the phone.
Conclusion
By now, we have covered three brilliant spying tools that will answer your question about how to hack a phone remotely. While all the three apps- mSpy, Minspy, and Spyier are amazing and offer a user-friendly interface, it’s normal to be confused about which app to go for. So here’s the conclusion.
Clearly, mSpy is highly recommended since it’s cheap and offers 36+ spying features. The list of features offered by Spy is longer than the other two apps. Additionally, getting started with mSpy is way easier than the other rival apps.
mSpy leaves no room for being caught while intruding on someone’s device. Additionally, customers might be entitled to occasional promotional offers that the mSpy developers offer. That’ll help you save money on subscription plans. The user interface of mSpy lists all the tools in a single place. While in the case of other apps, even a simple setting might be buried deep, which hinders the user experience.
The level of details produced by mSpy is higher than its rival apps. Using mSpy will allow you to gather all the basic and minute details of the targeted device in no time.

 How to Open a Snap without Them Knowing in 2023?
How to Open a Snap without Them Knowing in 2023?  How to Hack a Tiktok Account in 2022? (8 Different Smart Ways)
How to Hack a Tiktok Account in 2022? (8 Different Smart Ways)  How to Use the Best Kik Hacking App: 3 Kik Hacking Solutions
How to Use the Best Kik Hacking App: 3 Kik Hacking Solutions  How to Hack Yahoo Mail Password?
How to Hack Yahoo Mail Password?  Can Skype be Hacked: Find Out How to Hack a Skype Account Here
Can Skype be Hacked: Find Out How to Hack a Skype Account Here  How to Hack Gmail Account in 2022?
How to Hack Gmail Account in 2022?  5 Ways to Find Address with Phone Numbers
5 Ways to Find Address with Phone Numbers  How To Check For Scammer Phone Numbers?
How To Check For Scammer Phone Numbers?  Best TikTok Tracker Apps for Parents in 2022
Best TikTok Tracker Apps for Parents in 2022